By Bill Knapp
Heed this warning! You may not be bound to comply with regulatory requirements, such as HIPAA, PCI-DSS, FERPA, Gramm Leach Bliley, Sarbanes Oxley or GDPR, but failing to invest the time and resources in preparing for a cybersecurity incident could be the death knell for your business. Various studies and reports indicate that a significant number of small companies are unable to sustain their businesses over six months after a cyber attack. What can we do and where can we turn to avoid becoming a statistic?
The NIST1 cybersecurity framework with its practical set of guidelines has been structured and published to specifically help businesses become more resilient. The framework formally became a federal act last August requiring all federal agencies to implement and follow this structure. For small businesses it is voluntary. This program provides a set of standards, guidelines and best practices to manage cybersecurity-related risk. In the grand scheme of things it is an initiative to protect the critical infrastructure important to our economy and national security.
This work may often feel like overhead and a burden to the business, but you likely have your trusted advisors for issues pertaining to law, finance, insurance, human resources and IT who can help. However, at the end of the day, the burden of managing cybersecurity lands squarely on the business owners—those who are directly responsible for the survivability of the organization.
Due to the increase in cybercrimes, you may just be hearing about the NIST Cybersecurity Framework for Small Businesses. Small businesses are increasingly adopting the NIST framework as their own to provide the structure for assessing and implementing their own security practices and systems. Five years ago it was first issued as an Executive Order to enhance the security and resilience of the nation’s critical infrastructure. Although only five years in existence, the core of the framework is based on existing and validated standards, guidelines and practices that are tried and true.
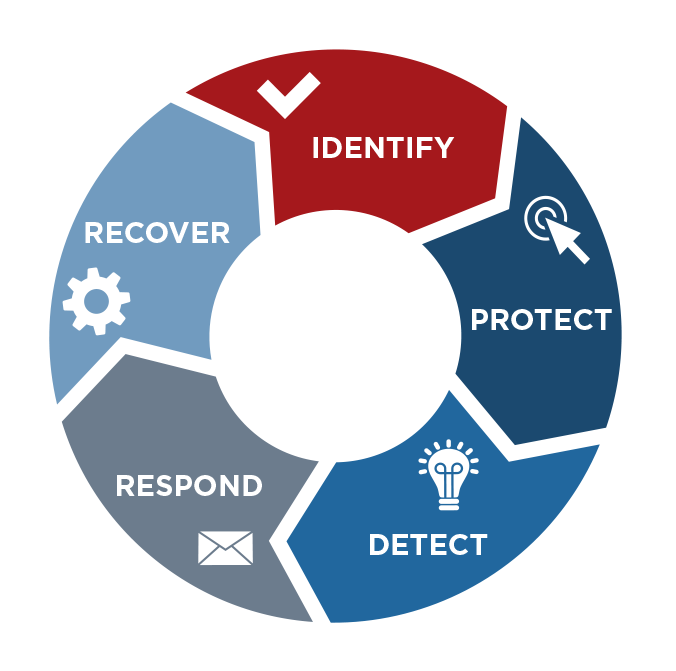
To make this useful, let’s break it down. There are five logical functions, each embedded with categories, subcategories and references to guide business owners and staff to build security and resiliency into their organization.
Identify – “Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.”
-
Asset Management
-
Business Environment
-
Governance
-
Risk Assessment
-
Risk Management Strategy
Protect – “Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services.”
-
Access Control
-
Awareness and Training
-
Data Security
-
Information Protection Processes
-
Maintenance
-
Protective Technology
Detect – “Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event.”
-
Anomalies and Events
-
Security Continuous Monitoring
-
Detection Processes
Respond – “Develop and implement the appropriate activities to take action regarding a detected cybersecurity event.”
-
Response Planning
-
Communications
-
Analysis
-
Mitigation
-
Improvement
Recover – “Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event.”
-
Recovery Planning
-
Improvements
-
Communications
To be totally honest with ourselves, there is no destination when it comes to cybersecurity. It’s a journey. A journey that presents many turns and obstacles all along the way. It always has and it is likely that it always will. However, if we follow a plan (i.e., the NIST CSF framework), it can lead us to a better and more secure place by providing:
-
A comprehensive set of cybersecurity policies and procedures
-
A remediation plan for present vulnerabilities
-
Guidelines for regulatory compliance, if required
-
A plan for implementing a security infrastructure to detect and protect your digital and financial assets
The first step on this journey will be to develop a Framework Profile that will identify the outcomes that your business will develop from the categories and the subcategories, based on your risks and your needs, all very specific to your business, your market sector and your industry.
In developing your Framework Profile, you will want to start with an assessment. The simplest and best first step will be a self-assessment. The goal will be to arrive at a quick sense of your strengths and weaknesses and to provide advice as to what improvements you should consider. Think about an assessment that will measure your results against the NIST model for cybersecurity for small business.
An assessment that reasonably balances a discovery that is both practical and comprehensive is a good start. Some sample questions may include:
-
Do you require Information Security training for your employees?
-
Are recovery processes and procedures documented and reviewed?
-
Are potential impacts from third parties identified and documented?
-
Are you using an email filtering solution?
-
Do you have web filtering or website blocking set up?
-
Do you have a threat detection product in place today?
-
Are you monitoring your IT environment for anomalous events?
-
Does your organization have an internal process for assessing risk?
The answers to these and other questions will establish your current state and your current security posture, both from a technical and an organizational standpoint. It will also be useful to have an understanding and comparative analysis of how your business stacks up overall, by industry, by size and by location.
The results of the assessment should at a minimum establish the gap analysis for the systems, policies and procedures that will require remediation and improvement. Understanding the importance of each of these and other factors will also help to set your priorities, the plan and the budget for what will create the best results with the greatest impact and return on investment.
With the results of this assessment in your hands, the next best step will be to meet with your trusted advisors who can then counsel you on the subsequent steps, which should include going over the results and running through the assessment together to get a deeper look. After all, this practice of assessing your risks should be approached as a longitudinal study and conducted regularly over time. Everything having to do with cybersecurity is very dynamic. Your business is likely changing from month to month and year to year. The marketplace and economic environment is ever-changing. Certainly, the vulnerabilities and threats to the security of our digital assets are changing daily with new forms of attacks.
The Final Word… of Warning
We have all witnessed the US government and large corporations with highly staffed, world-class, expert security teams fall victim to data breaches costing millions of dollars. It’s very clear that no one organization is 100 percent immune from cybercrimes. We also know that attacks directed at small businesses are on the rise. Please pay extra due diligence to planning for the fifth function: Recover. Have systems and a plan in place to recover your systems, recover your data, recover your reputation and recover or insure against any financial loss.
SBAM has a solution to help small business owners detect cybersecurity risks. Learn more!
Bill Knapp is Program Manager for NuWave Technology Partners. He brings over 25 years of experience in building successful teams and programs in the Information Technology industry. His expertise in information security comes as a result of building programs and practices that have served clients over the years with a wide range of security services, ranging from security assessments and systems design to business continuity planning and managed security solutions.